Authentication
Endatix provides a flexible authentication system supporting multiple providers. By default, the system uses the internal JWT based provider ("Endatix JWT"), which stores the user information in the database. It's easy to add additional authentication providers.
We have a list of providers that we support with ability for you to add custom providers:
- Google OAuth
- Keycloak
Authentication Flow
The Endatix Hub is the frontend application that users interact with, while the Endatix API is the backend application that handles the authentication and authorization. Here is how the authentication flow works:
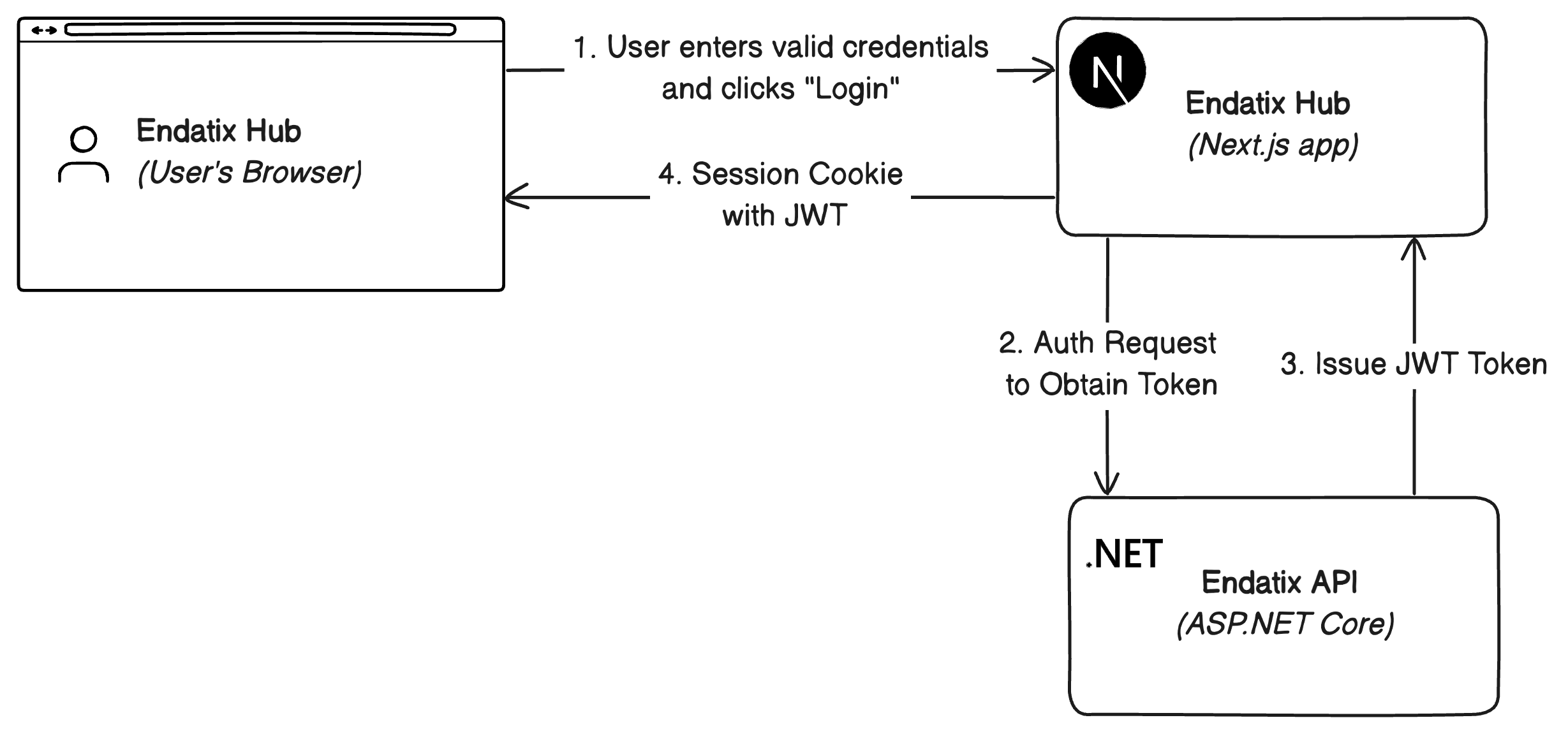
- User Authentication: User signs in via Hub using any configured provider
- Provider Validation: Provider validates credentials (OAuth/OIDC/JWT)
- Session Creation: Hub creates secure server-side session
- API Communication: Hub uses session to authenticate API requests
- Token Management: JWT tokens handled securely on server-side
When external authentication provider is used (e.g. Keycloak, Google OAuth), both the Endatix Hub and Endatix API will act as relying party for the external authentication provider and using the issued JWT tokens for authentication.
Customization Flow
Very high-level, here is how quickly you can set up and customize authentication for your needs. Detailed guides are available below.
- Endatix API
- Endatix Hub
One line of code to enable custom authentication providers. Just modify the Program.cs file to add your custom providers.
var builder = WebApplication.CreateBuilder(args);
builder.Host.ConfigureEndatixWithDefaults(endatix =>
{
// Add Google OAuth provider
endatix.Infrastructure.Security.AddGoogleAuthProvider();
// Add Keycloak provider
endatix.Infrastructure.Security.AddKeycloakAuthProvider();
// Built-in JWT provider is included by default
});
var app = builder.Build();
app.UseEndatix();
app.Run();
Register providers for the Endatix Hub by modifying the authentication configuration file (endatix-hub/auth.ts) is very easy. We use Auth.js for the frontend authentication framework, giving you easy access to 80+ auth providers.
All you need to do is register the providers you want to using the authRegistry passing a provider with default or customsettings.
import NextAuth from "next-auth";
import { authRegistry } from "./features/auth/infrastructure/auth-provider-registry";
import { createAuthConfig } from "./features/auth/infrastructure/config-factory";
import {
GoogleAuthProvider,
KeycloakAuthProvider,
} from "./features/auth/infrastructure/providers";
// Register authentication providers
authRegistry.register(new GoogleAuthProvider());
authRegistry.register(new KeycloakAuthProvider());
// Create NextAuth configuration
const authConfig = createAuthConfig(authRegistry);
export const { handlers, signIn, signOut, auth } = NextAuth({
...authConfig,
});
Provider Setup Guides
Below are the detailed setup guides for each provider. Choose your authentication provider and follow the detailed setup guide:
Endatix JWT Customization
Registered by default, it's available at any time you start the application. Here is a complete guide to customize the built-in JWT provider:
- JWT settings configuration
- Secure key generation
- Custom claims and roles
Keycloak Setup
Keycloak is very powerful and popular open-source option for supporting multiple authentication scenarios. Read the complete guide to setting up Keycloak authentication for your Endatix application:
- Keycloak realm and client configuration
- OIDC endpoint setup
- User management and testing
Once you have basic Keycloak authentication working, explore advanced features in the Guides section:
- Session Bridge - Cross-platform token exchange
- External Authorization - Authorization concepts and benefits
Google OAuth Setup
Google OAuth is a very popular and easy to use authentication provider. Read the complete guide to setting up Google OAuth authentication for your Endatix application:
- Google Cloud Console configuration
- Environment variables setup
- Testing and troubleshooting
Related Topics
- Authorization - Learn about authorization in Endatix and role-based access control